Recent Uptick in Akira Ransomware Incidents Serves as Reminder to Follow Safe Cyber Practices

Printable pdf: SafeAlert-Akira Ransomware Uptick. Follow Safe Cyber Practices SA31
We have seen an increase in the number of banks reporting Akira ransomware attacks. As one of the most sophisticated and prolific ransomware groups active today, the Akira ransomware group executes a double extortion method by both freezing networks and threatening to publish exfiltrated data.
Recent attacks exploited a commonly used SSL VPN connection service/product. It is recommended that I/T staff should ensure that all patches are implemented and be on alert for network anomalies.
The Akira attack method usually involves the following steps:
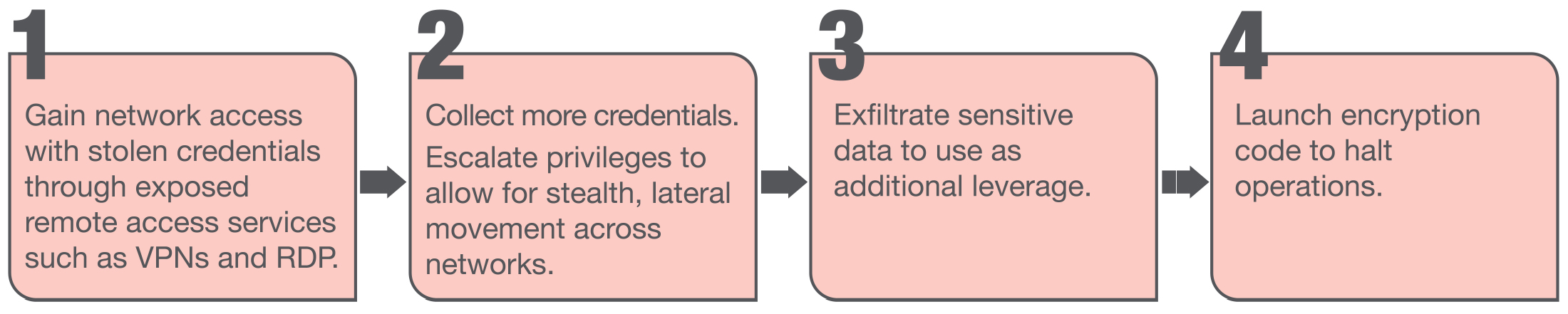
Common Akira network intrusion methods and corresponding prevention techniques include:
Technique | Prevention |
| Phishing Emails | Email Security: Deploy advanced spam filters and educate users about phishing risks |
| Vulnerability Exploits | Patch Management: Regularly update software and hardware to eliminate known vulnerabilities. |
| Credential Theft | Access Controls: Enforce strong authentication, limit administrative privileges, and implement least-privilege policies. |
| Malicious Scripts | Network Segmentation: Separate critical systems to reduce lateral movement by attackers. |
66e06ecd-f855-4119-b784-193811937ddc.svg?Status=Master&sfvrsn=448913a7_3/
ABAIS-Logo-1-(1)66e06ecd-f855-4119-b784-193811937ddc
.svg)